About three years ago, I wanted to login into an installation of CrazyStat which I had installed back in 2004 in CrazyStat’s early days. Problem was, I had forgotten the password. Of course I could simply change it, but I was curious what the password was and if I would be able to find out. The old version of CrazyStat installed on that server saved the password as an MD5 hash, but without any salt (new versions save salted passwords). So the challenge was to decrypt an MD5 hash which had not been salted before hashing.
I looked the hash up in several rainbow tables I found on the web, but did not find any match. Of course, I had not used a simple password, so rainbow tables including dictionaries and brute-force up to several characters were useless.
So I thought, well, let’s brute-force it myself. So I wrote a simple brute-force algorithm and let it run on the Hash. I included characters, German special characters (öäüßÖÄÜ), numbers and several other special characters I though I might have used in the password. So this resulted in a huge character set (>80 characters) and a very slow brute-force. I ran it on my home server for several days, but did not succeed. I think I was brute-forcing passwords of 9 characters when I stopped.
I just gave up at that time, because it was not that important and just an experiment.
Lately, I read that Google is a very good password cracker. Thinking about this, it is obvious: Google indexes the whole web, and there are several MD5 rainbow tables on there, which Google indexes as well. So just google for a hash, and if it is in one of the rainbow tables indexed by Google, you will find it. Also some pages use MD5 for page-IDs which will be indexed by google as well. So I enter the hash I had tried to decrypt three years ago, and it just gave me the password I had searched for straight away! Far more efficient than brute-force or downloading rainbow tables 😉 By the way, the password I searched for had more than 9 characters and is not included in any normal dictionary, although maybe in some password list (but not frequently).
I tried several other hashes to see how good Google is. Of course all easy ones are included. But some other more challenging ones were included as well. For example, it knows the hash of “crazystat” (“CrazyStat” is not in there so far). It knows the hash of my hometown (I will just give you the hash here, find out yourself: 97b559a3d65b95dcda14d70e49ef87fc).
So compared to most rainbow table lookups I have seen so far, Google performs very well. Of course not everything is in there, and with a good salt string, it should be useless.
One test I tried were some random characters, but not so many. I was surprised that Google does not know it. I then used a decrypt/encrypt site that stores every hash it calculates when you encrypt something in a rainbow table. Afterwards, this site was able to decrypt it of course. Now I am waiting how long it takes for Google to index that hash as well.
Now let’s see whether you are faster: Here is the hash:
f533abf87579c6ccc8de45c4d81e9e39
A simple brute-force or a good rainbow table should do to decrypt that. Please leave a comment if you decrypted it. There is at least one md5-decrypt site now that knows this hash, so you might also be able to find this one.
Have fun!
And of course, never be the bad guy who uses stuff like this meaning ill 😉
Update 2012-09-22: It seems so many people google the hash I posted here that Google suggests it automatically when searching for f533:
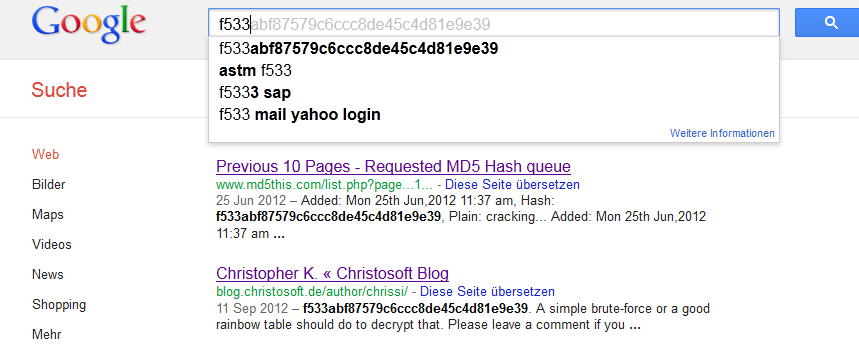
But MD5this did not crack it yet and it seems Google is not able to index the md5lookup site I fed with the hash. Well, probably the hash is a bit more difficult to crack than I thought. But somebody must be able to decrypt that. Come on!